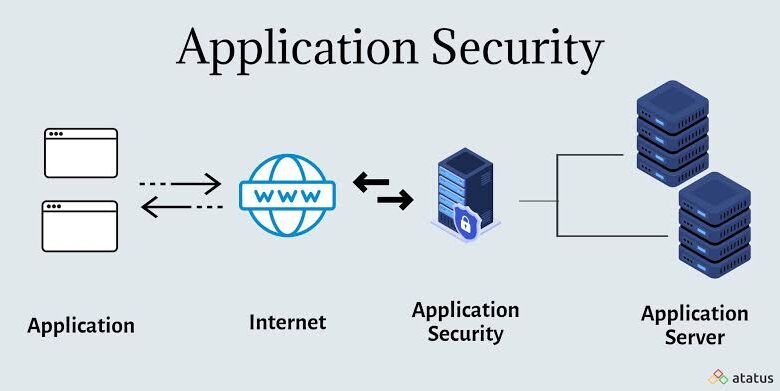
Application security is a critical aspect of social development as a major chunk of organizations tend to have dedicated AppSec programs. In the last few years, there has been a major cultural shift with application security going on to become a strategic initiative which spans departments and not an activity.
Numerous factors are driving the surge of app sec with a broader strategic program that incorporates the evolving threat landscape, as recent trends become deliverable as code with security and infrastructure following the same module. With the development of software development, application security has to further shift in the process and the products can reach the customers in the hand.
More about application security
Attackers have gone on to evolve with technology. with an increase in digital transformation across industries, they have realized that you shouldn’t focus on individual targets. It makes sense to make use of the vendor targets. More than ever before clients are asking about the information security program of the vendors since their security depends upon the product they trust. This means that if you are releasing the product and gaining the trust of customers there is a need to build an application security program.
The things that an application security program is expected to address
An application security program can address a wide range of security vulnerabilities. This is a strong place to start and you need to turn the focus of your application development program to OWASP 10 an industry that goes on to represent the most pressing vulnerabilities. This goes on to showcase the vulnerabilities that are part of the applications. When you take into consideration the real security landscape, a recent view has gone on to shift to a broader view of what the exact meaning of application security means.
The part of application security means the code-level security. Code-level issues turn out to be classic vulnerabilities that you think along the lines of penetration testing. Such issues go on to include validation programs like SQL injection and cross-scripting along with other problems like remote code execution. These are issues that relate to using insecure methods in code and are often addressed with code scanning or a secure form of code training.
A point to consider is that application security begins even before the first code is written. Apart from the instructions on a piece of paper, a program has to relate when it comes to a couple of choices in the manner by which the application solves problems. If you are looking to solve design-level problems at an initial planning stage you need to perform threat modelling along with the new features that are being added. Then the threat model can inform the choices when it comes to frameworks, libraries, and cryptography when it comes to solving each problem.
Processes
A team will not be able to develop secure software without a secure build process. The reason is that the build process is all about what the developers end up doing day and night for the product creation that the customers have gone on to trust. The secure build process has to be documented and revisited to embrace the best of security practices though this is only a part of the story.
The reason is that the process documentation is not going to stop an attacker. Being part of the build process, you have to ensure that developers are following those security programs when you are building software. There is a need to monitor what they are doing daily and go on to improve coverage and compliance when it comes to the policies themselves.
Technology
Technology is not the entire piece of software security it has an important role to play in the software security picture. Modern software development is dependent upon external libraries so the security of the software evolves on the chosen libraries and their implementation properly. It does make sense to make it easy for the developers to use a secure build environment. What this means is that the teams should be using automated tools which set the tone for properly employing virtual environments and hardened containers
As part of the mobile application security model security is also important. The software teams should be conducting a static analysis throughout the process. What this means is that they would be able to conduct security vulnerabilities along with the development of features. Since the version of the software comes close to release. Even security automation would also point to the employment of virtualized environments and containers which is much more than that.
The trends in application security
Once you are building your application security program you have to keep the following trends in mind
Security champions
In the last few years, security champion programs have gone on to soar in popularity. One of the reasons is that they have to scale up capabilities and culture during the various parts of a business. A few security experts will never be able to build security when it comes to the scale of an entire business. This may turn out to be a major problem as more and more responsibility of security is shifted from a dedicated security program towards a daily operation of the product teams. Once you have a security champions program in place, a central application security program will be able to work with the security champions. They will be working with their team to strengthen the core security features.
Threat modelling
The evolution of threat modelling is evolving. The logic is that one of the security experts may get on board and figure out the potential threats against the product. But still security experts will be able to figure out which is the best thing to do that means how much you should be doing it manually or using other tools.
To conclude since there is an increased focus on supply chain security, customers have never gone on to care about application security programs of companies. There is handy professional help available at various points.